The Foundations of Zero Trust
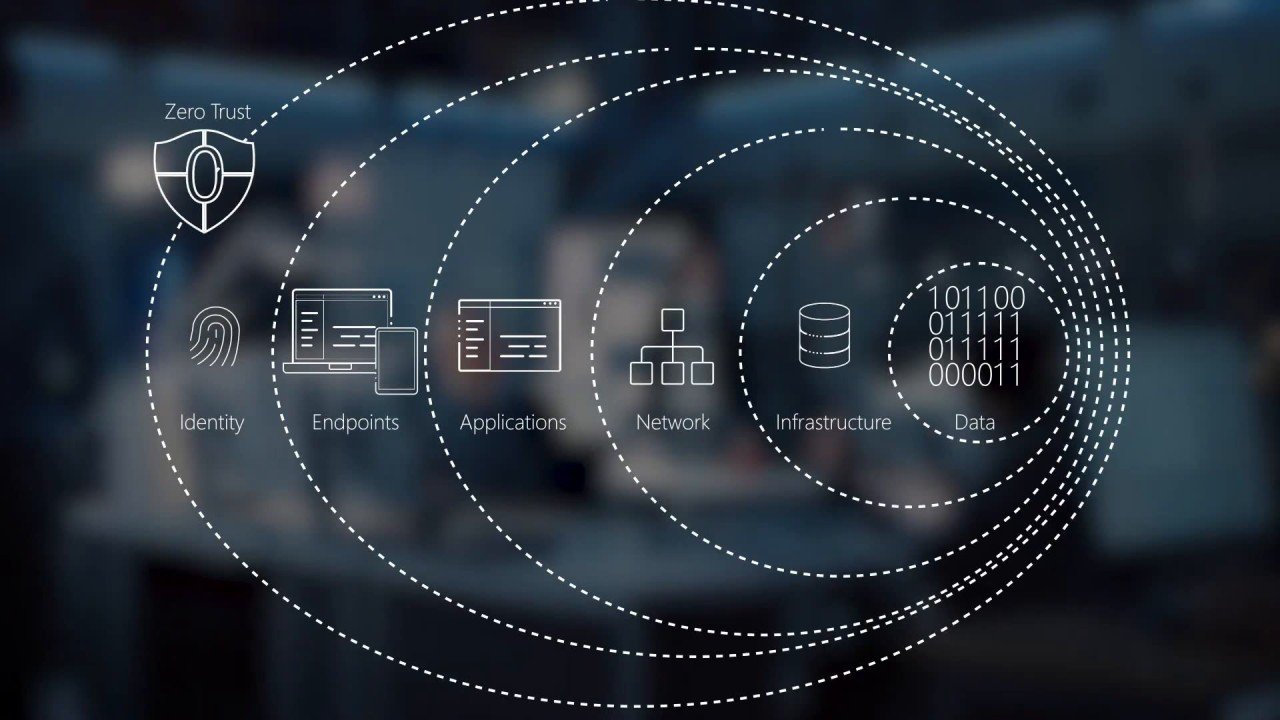
A cyber security approach of verified identity and least privileged access requires specific capabilities in the underlying infrastructure, without which it is impossible to safeguard today’s distributed, digital enterprise
The days of firewalls and the internal network being the defining characteristics of enterprise security are long gone. Today, distributed resources, hybrid infrastructure and remote users all conspire to make the cyber security landscape more challenging and complex.
However, there is a security model that has been around for decades but is now being adapted and applied to meet these various needs, providing a model for protection for today’s enterprise: Zero Trust.
Emerging Model
While the term and concept for the Zero Trust Model (ZTM) has been around since 1994, when it was first expounded in a doctoral thesis, It was in 2009 that it saw a major application with Google’s BeyondCorp. Since then, it has seen creeping adoption. In 2021, it was the Biden Administration’s executive order on cybersecurity that insisted upon it to “improve the nation’s cybersecurity and protect federal government networks”. That executive order became the US Federal Zero Trust Strategy, embodied by the US Cybersecurity and Infrastructure Security Agency (CISA) Zero Trust Maturity Model 2.0. Already, other nations such as Australia and Canada, are starting to adopt the ZTM.
According to Statista, 41% of respondents to a global survey in 2022 said they had plans to adopt a ZTM and were already started on implementation, while a further 39% said they had plans to do so.
Across Europe, according to Forrester, more than a third of organizations have a zero trust strategy. Gartner predicts that more than 10% of large enterprises will have a mature ZTM in place by 2026, with more than 60% of organizations embracing zero trust “as a starting place for security” by 2025.
Principles
The principles of a zero trust model are relatively simple. Firstly, the identity of each user, device and service is verified before any access is granted, irrespective of where that entity is coming from.
Secondly, even when verified, an entity is given the least level of privileges necessary to accomplish whatever task or role they have been assigned under the security policy that applies.
Finally, traffic and information access is based only on explicit policies, roles and tasks, with all other access and traffic blocked.
The other key aspect of the ZTM is to assume a breach can occur, and to act accordingly. This means that measures are taken to ensure that a breach can be contained, minimized, and identified. According to Microsoft, by assuming a breach an organization can “minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.”
Building Blocks
A key aspect of a ZTM is a network that can be segmented by policies in a sophisticated and granular manner. This means that should a breach occur in any one segment, it cannot spread to another or exfiltrate assets that have been compromised.
Network segmentation can not only improve security, it can also improve efficiency and speed, as only necessary requests are allowed, minimizing traffic and processing.
However, network segmentation must also be adaptable, to be able to cope with evolving needs and agile enough to facilitate new services and business models.
Network access control (NAC) is another vital element for a ZTM. Users, devices, and end points must all be verified under various criteria to ensure identity and authorization. This is especially important in today’s world where workers can be working from home, a client site, a remote work hub, or on the road from a hotel room, airport or in the open air via 5G.
Identity and Access Management (IAM) combines with NAC to allow posture checking, time and place rules to apply also. If a user logs off in Dublin and reappears 20 minutes later on a different machine with a distinct OS from Kuala Lumpur, then an IAM system will flag the anomaly and report accordingly.
Security Information and Event Management (SIEM) systems also help in such instances to appropriately orchestrate and apply the user, device and data access policies and requests as part of the ZTM.
ZTM Foundations
While none of these systems, NAC, IAM or SIEM, are anything new, their usage in a ZTM requires a different architecture compared to more traditional approaches. And it must be borne in mind that today’s enterprises are almost entirely hybrid, consisting of on-premises, cloud, and increasingly, edge computing deployments.
In fact, a combined estimate from IDG and Forrester suggests that by 2025, a digital enterprise will likely comprise 20% on premises IT, 30% on the public cloud, and 50% at the edge.
Applying these measures in such a complex environment will require a robust, resilient, and modern IT infrastructure, where interoperability, visibility and granular control is critical.
Unless an organization can see, analyze, and orchestrate every element of its estate, it has little hope of applying a ZTM to protect it all, as well as facilitating the kind of agility and adaptability required in today’s volatile market conditions.
Only by deploying a smart, modern network infrastructure can an organization employ the tools necessary to bring together these elements and successfully implement a zero trust model. Legacy networking systems that do not support policy-based segmentation, network access control and identity and access management, or direct interoperability with cloud services, will stymy ZTM goals.
Culture Considerations
There is one more aspect of ZTM that cannot be overlooked and that is culture. The assertion that ‘culture eats strategy for breakfast’ is often attributed, however accurately, to Peter Drucker. However, the implication is that if an organization has a culture that is predominantly against a zero trust security approach, it has little chance of success.
What this means is that in implementing a ZTM, it is critical to educate users, at every level, as to the benefits of the model, and the critical part they play in it. It is often said that a well educated user is as effective a security actor as any technical measure, and this is just as applicable for ZTM.
While zero trust may have negative connotations initially, when it is fully explained to users, they can often become its greatest advocates. Early, inclusive information and education programs ensure that users understand the approach, the measures, and their responsibilities within it.
Zero Trust Future
Tomorrow’s enterprise will not be kept safe by today’s security. ZTM is a new mindset that requires organizational, technical, and cultural change.
In today’s digital, distributed enterprise, where users need to be accommodated to work as they desire, competing in volatile markets where agility and speed can be critical, a zero trust model has the potential to meet these competing needs without stifling innovation.
However, a ZTM can only be implemented on a foundation of a smart network infrastructure commensurate with its requirements.

Related Resources
Transforming Sports & Public Venues: Connectivity to Actionable Insights
When attending a game or event, guests expect a fast and stable mobile experience. This baseline goal has grown and evolved substantially, as more customer-facing and back-of-house assets are digitized in venue environments, relying on critical IT network solutions...
ArcelorMittal Improves IT Performance and Reliability Across Three European Corporate Hubs
ArcelorMittal is the world's leading steel and mining company with a presence in 60 countries and an industrial footprint in 19 countries worldwide. It employs over 4,000 staff, 800 of whom are based in its head office in Luxembourg. It employs over 4,000 staff, 800...
MSK Group is Ready for Tomorrow With Modernized Network
MSK Group is a family-owned business based in Ylihärmä, Finland. For more than 70 years, it has been manufacturing high-quality plastic components, mobile machinery, and smart cabins for a range of industries, including construction, mining, agriculture, forestry, and...
Digital Transformation Efforts Powered by Network Automation, Simplicity, Security, and Intelligence
ŠKODA AUTO, based in Mladá Boleslav, is a leading industrial enterprise in the Czech Republic and one of the oldest carmakers in the world. Today, ŠKODA AUTO employs over 30,000 people, operating as part of the Volkswagen Group for nearly 30 years. In recent years,...
Streamlining the Kraft Group’s Manufacturing Operations
The Kraft Group is a privately held holding company headquartered in Massachusetts. It is the holding company for several subsidiaries operating in various sectors, including manufacturing and sports. Extreme Networks has partnered with the Kraft Group for over a...
Extreme Networks meets Major League Baseball™ at the intersection of Cloud, Mobility, and Analytics.
From the concourse to the dugouts and beyond — Extreme Networks is coming to a ballpark near you.CLOUD-SPEED Baseball and technology require agilityand flexibility without losing functionality. MOBILITY Mobile and IoT Devices are integral toplayer and fan experience....
Seattle Seahawks Achieve Operational Freedom with Cloud-Managed Wi-Fi
Lumen Field is a world-class football/soccer stadium and exhibition center, home to the Seattle Seahawks. The 325,000 sq. ft. complex seats 70,000+ and hosts a wide variety and volume of events each year from trade shows, corporate events, concerts, and more, making...
MLB All-Star Week Drives Record Wi-Fi Fan Engagement
MORRISVILLE, N.C.--(BUSINESS WIRE)--Jul. 18, 2023-- Extreme Networks™, Inc .(Nasdaq: EXTR), a leader in cloud networking, today announced that the recent MLB All-Star Week in Seattle, which ran fully on Extreme wireless solutions, drove record fan Wi-Fi engagement...
Baylor Outfits New Stadium with Professional Grade Wi-Fi for an Interactive Fan Experience
McLane Stadium is the home football stadium of Baylor University, a private higher education institution located in Waco, Texas. Devoted to delivering an exceptional gameday experience to its fans, in the fall of 2012 Baylor University embarked on a $260 million...
Always On” High-Density Wi-Fi and Analytics for Stadiums and Arenas
Fans everywhere want to share their sports experience and excitement with other fans in the stadium, their friends and family at home, and their social networks, providing reliable, wireless internet access was crucial to delivering a world-class fan...











